Big Brother goes by a new name these days – Big Data. That’s
the term for the process of collecting your sensitive – and sometimes
confidential – information. With more
and more people online and using high tech in their daily lives, it’s hard to
ignore the Big Data knocking on the front door.
There are news reports, lawsuits, and shocking secrets revealed nearly
every week about who’s accessing our data like never before.
In general, there are two entities that have an interest in
gathering as much data as possible about your life: Law enforcement and private
companies. Law enforcement agencies
ostensibly collect data to identity and stop terrorist threats in the name of
homeland security. Private companies,
however, collect data to make money.
Let’s start with an obvious data thief – social media. Facebook is by far the largest social media
platform, estimated at a $100 billion company.
Google is valued even higher, at $300 billion. Yet, they are still free to the user. How is that possible? Facebook and Google aren’t in the business of
offering free services; they aggressively collect your data and “deliver it to
lucrative advertising platforms.”
And all of those free social media apps? How do they make money? By collecting and reselling your data. Have you noticed that they’re eager to have
you sign in with your Facebook login or email address? Every time you do that, they’re downloading
every tiny atom of your personal information stored within. Why is it that when you click on a link to an
article you see posted on Facebook it often opens the article within Facebook’s
“umbrella browser?” Facebook wants you
to stay in their platform so they can track what you’re looking at and clicking. Free is not free when you pay with your data.
Think about what kind of access to the nooks and crannies of
your life the cell phone companies have.
They have every single one of your texts, your phone calls sent and
received and the actual recordings, what you used your internet for, and where
you are with GPS.
10 major auto manufacturers – including Ford, GM, Nissan,
Toyota, and Chrysler - now collect data from your car’s GPS and onboard
computer for resale. Twitter, Yelp,
Foursquare, and Instagram, and many others have been caught mining address
books in smartphones without user knowledge or permission. It’s been estimated that up to 11% of free
mobile apps from iTunes do the same thing.
How omniscient is Big Data? When
Alexis Madrigal, a journalist for The Atlantic, started a big story on data
mining in 2012, she expected to find about ten companies who were collecting
consumers’ every online behavior. She
found 105.
What kind of data are they collecting on you?
Website activity - who you interact with, how long, and in
what capacity
What pages and posts you Like, share, and comment on.
Videos watched and uploaded online
Photos viewed, saved, and uploaded online
Cell phone conversations, numbers, and data
Mobile phone locations through GPS
All social media activity
Websites visited, how long, etc.
Emails sent and received
Mobile phone apps downloaded
Text messages sent and received
Skype video calls
Viber, What’sApp, etc. conversations
Online purchases
Credit card and debit card transactions
Financial information from bank accounts, retirement and
investment accounts, etc.
Court and legal documents
Travel documents
Health records
Credit score
Commuter tolls
Electronic bus and subway passes (Smartpass)
Education records
Arrest records
Bankruptcy records
Drivers license information
IRS records
Airport security information
Webcam footage
ATM video footage
Security video footage
What videos you watch on Netflix, etc.
What you buy on Amazon, Ebay, etc.
IP addresses of what computer you use, where it is.
Why should we worry?
The infringement into our privacy is a slippery slope into threats to
our civil liberty. With technology
evolving at a rate faster than laws can be written, the definitions of what’s
lawful and what’s clandestine are blurred beyond accountability, and the next
logical step, already unfolding, is to manipulate and control over behaviors,
not just spy on them.
Just as frightening, human beings are not even steering the
data piracy ship anymore. Companies use algorithms
to collect, analyze, and interpret our data in order to tailor our next Internet
search or usage. For instance, if you’re
doing a bunch of online research into vacations in Alaska, watch how quickly
Facebook starts posting ads for similar subject matter, or who quickly
Amazon.com, EBay, etc. will suggest similar content. Our every click is used to predict and steer
our future consumer behavior.
Did you know that Google even alters your search results
based on your past searches? The result
is a skewed access to information, that’s supposed to be neutral and universal,
and a skewing of information reality.
Analysts and watchdogs call the rise of cyclical data phenomena and
algorithms, “getting caught in a filter bubble.”
Your credit rating is based on an algorithm, as are airport
security procedures and IRS audits. But
when consumer behavior intersects law enforcement and even military action
based on algorithms, human beings are no longer making decisions. The National Security Agency uses monitors our
emails, phone calls, and bank records, and locations to try and identify
terrorists. But our military also uses
data and algorithms to target drones to deliver explosives in Pakistan and
Afghanistan, a practice highly criticized by the world’s human rights community
has.
As we found out when NSA whistleblower Edward Snowden turned
over sensitive NSA and CIA documents, the government has its hands in just
about data pie, forcing tech companies to turn over your data under the Foreign
Surveillance Intelligence Act. It was also
disclosed that the NSA collects millions of webcam images from Yahoo when users
thought they were completely private, many of them of an “Intimate, amorous,
and compromising nature.” Social media
companies like Google and Facebook as well as telecommunications companies have
entire departments dedicated to turning over data per government surveillance
requests. The phone carrier Sprint set
up a website in 2009 that allowed law enforcement to directly access users’ GPS
information. They received 8 million
governmental and law enforcement requests in the first year alone.
Now think about the potential danger of automating data
collection by adding advanced facial recognition software to the process. Does that sound like a far-out futuristic
conspiracy theory? What do you think the
“Tagging” of photos on Facebook is all about?
Of course, tech and other companies, law enforcement, and
governmental agencies say you shouldn’t be worried. One Google executive is on record as saying:
“Worrying about a computer reading your email is like worrying about your dog
seeing you naked.” However, your dog isn’t
taking photos of you and selling them online.
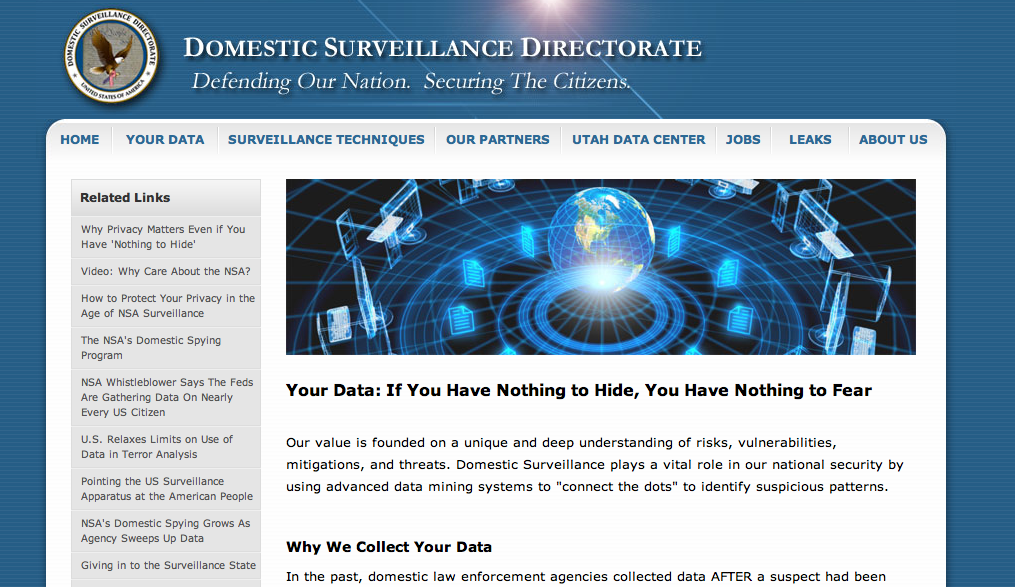
Or, to put the issue of trampling our privacy and civil liberties in Orwellian
terms, we can take notice of the advice from the Domestic Surveillance
Directorate, prominently displayed at the top of their public website:
“Your Data: If You Have Nothing to Hide, You Have Nothing to
Fear.”


No comments:
Post a Comment